Hacking Explained: DNS Spoofing
The Domain Name System (DNS) is generally used to map domain names and IP addresses. For example, let’s consider the following network configuration:
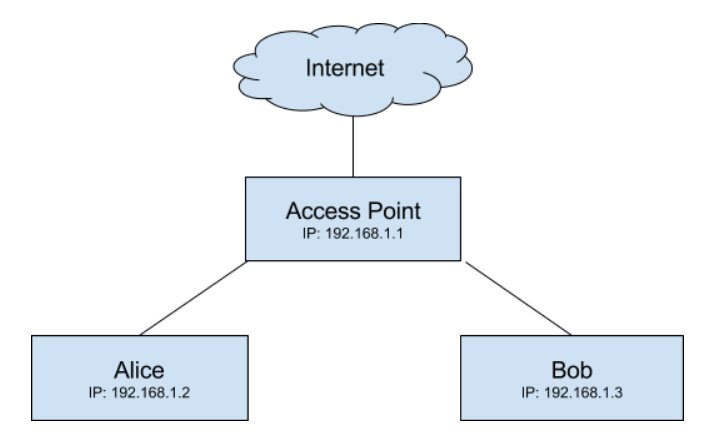
If Client A wants to request the content of https://www.google.com in their web browser, the request needs to be sent to an IP address corresponding to one of Google's web servers. If Client A hasn't previously saved (cached) an IP address for Google.com's web server, they will need to make a DNS query for the IP address assigned to Google.com. Which DNS server to use can be set manually on the client, but for our example let's assume Client A hasn't configured any. Most clients will use the DNS server as advertised by the Access Point that assigned them an IP address.
Often times the Access Point will also act as a DNS server and cache IP addresses for the domains it has previously queried. If the Access Point doesn't have a cached record of the IP address for Client A's DNS query, then it will need to forward the DNS query to the DNS server it is configured to use. Unless otherwise specified manually on the Access Point it may use an upstream DNS as advertised perhaps by the ISP. This chain (pictured below) continues all the way up to what is commonly referred to as a Root Name Server.
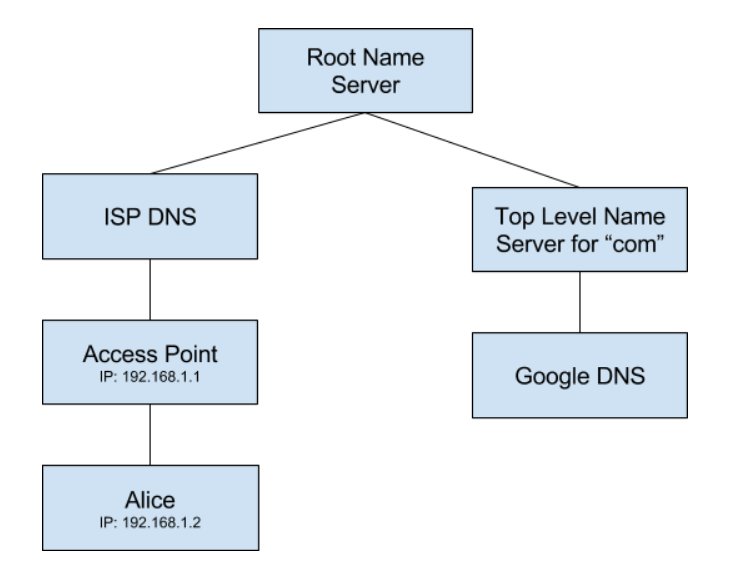
A Root Name Server will direct the DNS query to the top level name server corresponding to the DNS request. For example in the domain name www.google.com, the top level domain is "com". This top level name server knows which DNS servers to query for all domains registered as a ".com". Assuming the domain name being queried by Client A's DNS request is registered, it will eventually lead back down to one of Google's DNS servers. If Google's DNS server recognizes the domain being queried by Client A, it will respond with the IP address of a web server that their web browser can then use to fetch the contents of https://www.google.com.
DNS queries and replies currently do not use any sort of authentication or validation which opens up the opportunity for an attacker to spoof DNS replies. For example, let's assume an Attacker is acting as a man-in-the-middle between a Victim and the Access Point (for an example of this see my article on ARP Spoofing). Assuming the Victim hasn't manually set their DNS servers, they will automatically use the Attacker for DNS queries, allowing the Attacker to spoof the DNS replies with fake IP addresses and redirecting the Victim to web servers of their choice.
Here's a demonstration of how DNS Spoofing, ARP Spoofing and my URL Spoofing Trick for Chrome can be used to generate a pretty convincing victim scenario with my universal man-in-the-middle tool CopyCat. CopyCat is a proof of concept tool for attackers to circumvent the security provided by HTTPS and see/modify the traffic, and allow victims to continue to use the services provided by HTTPS web servers:
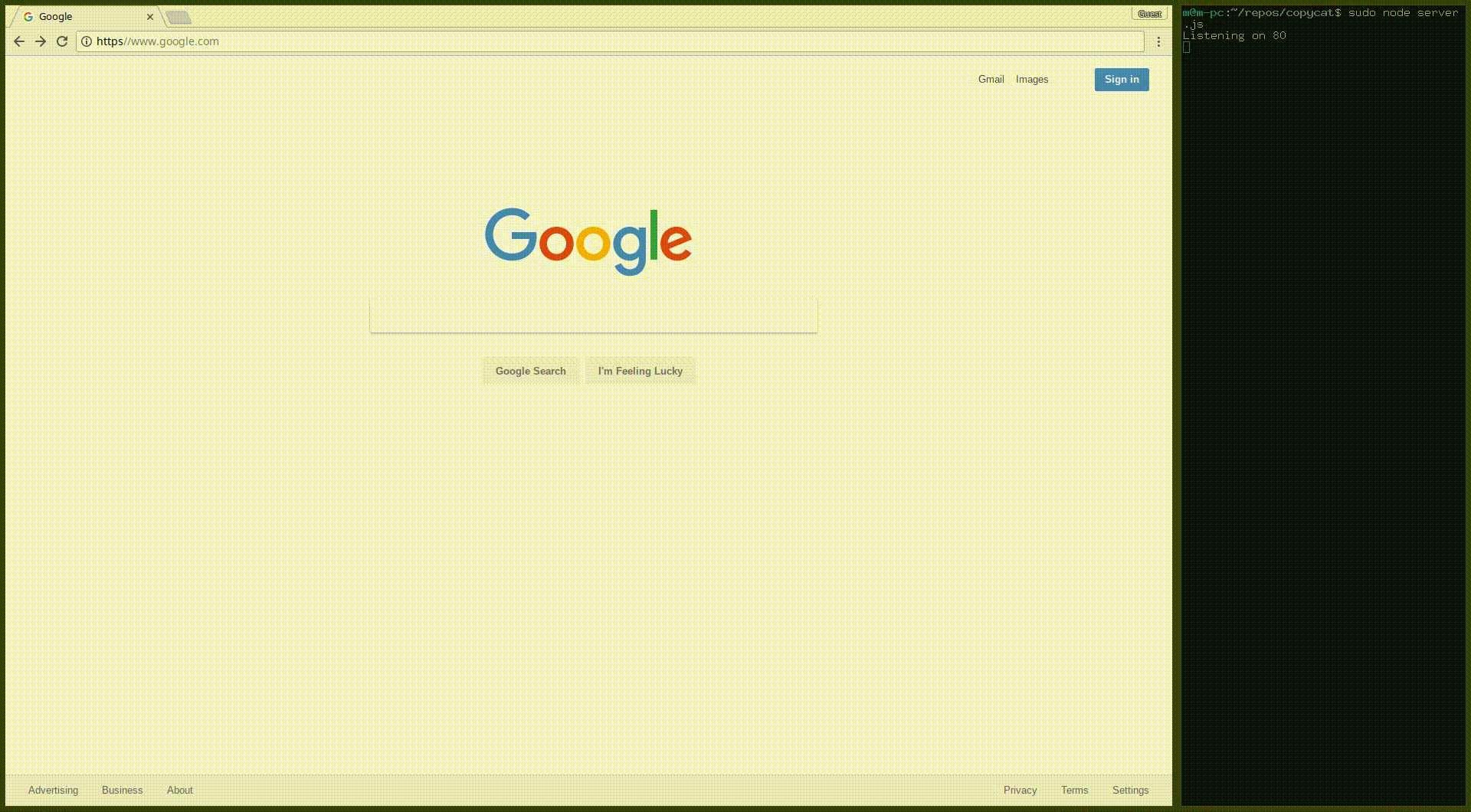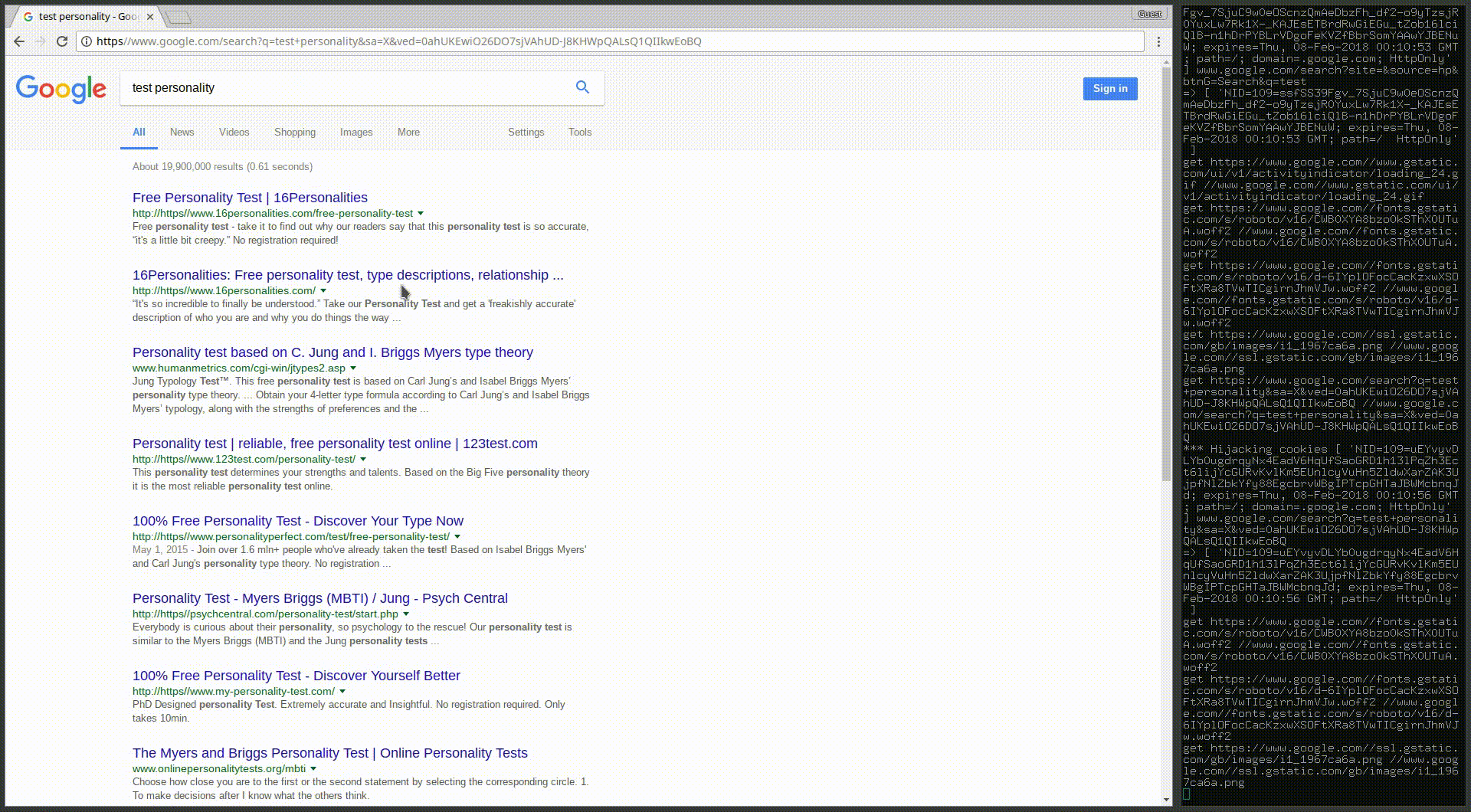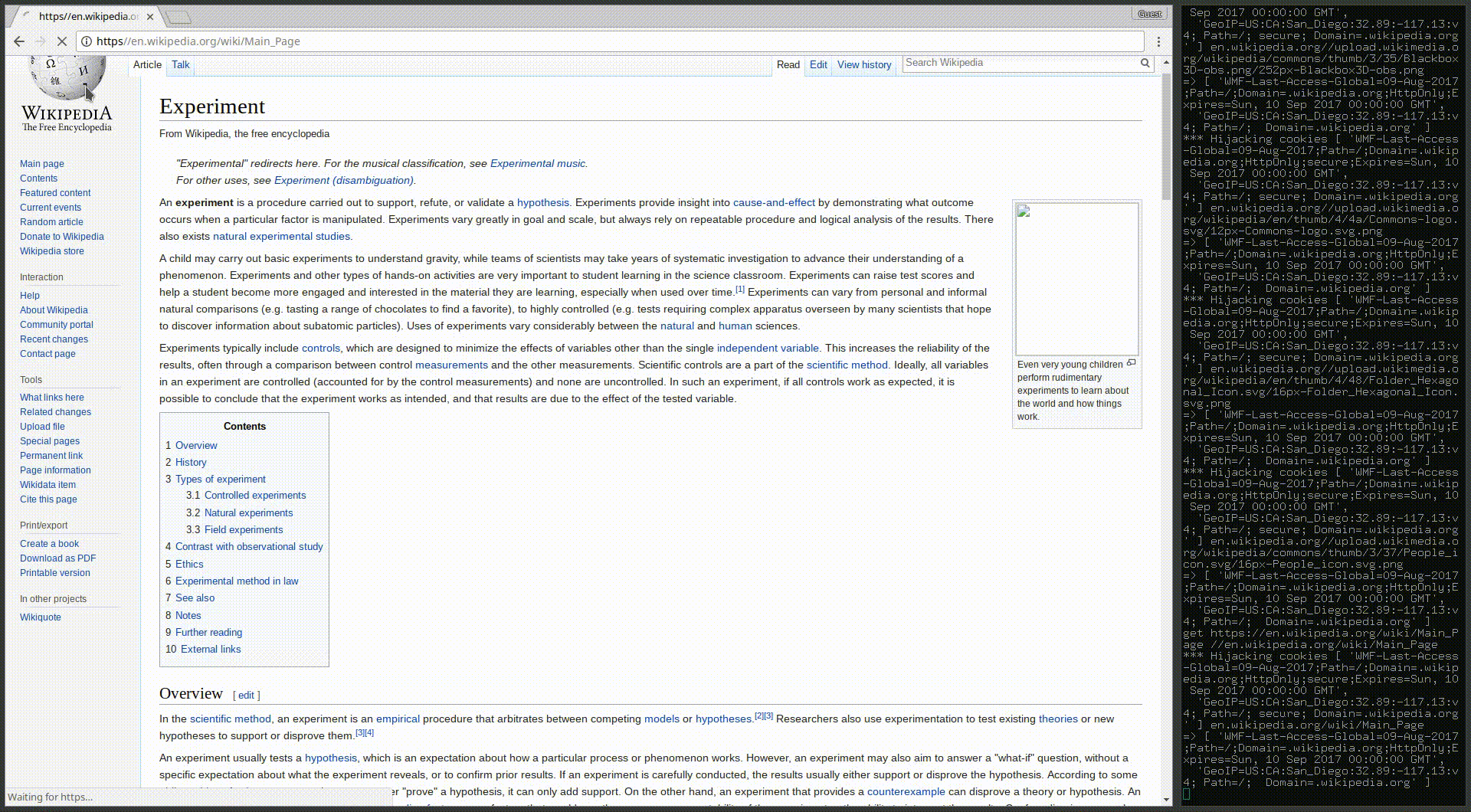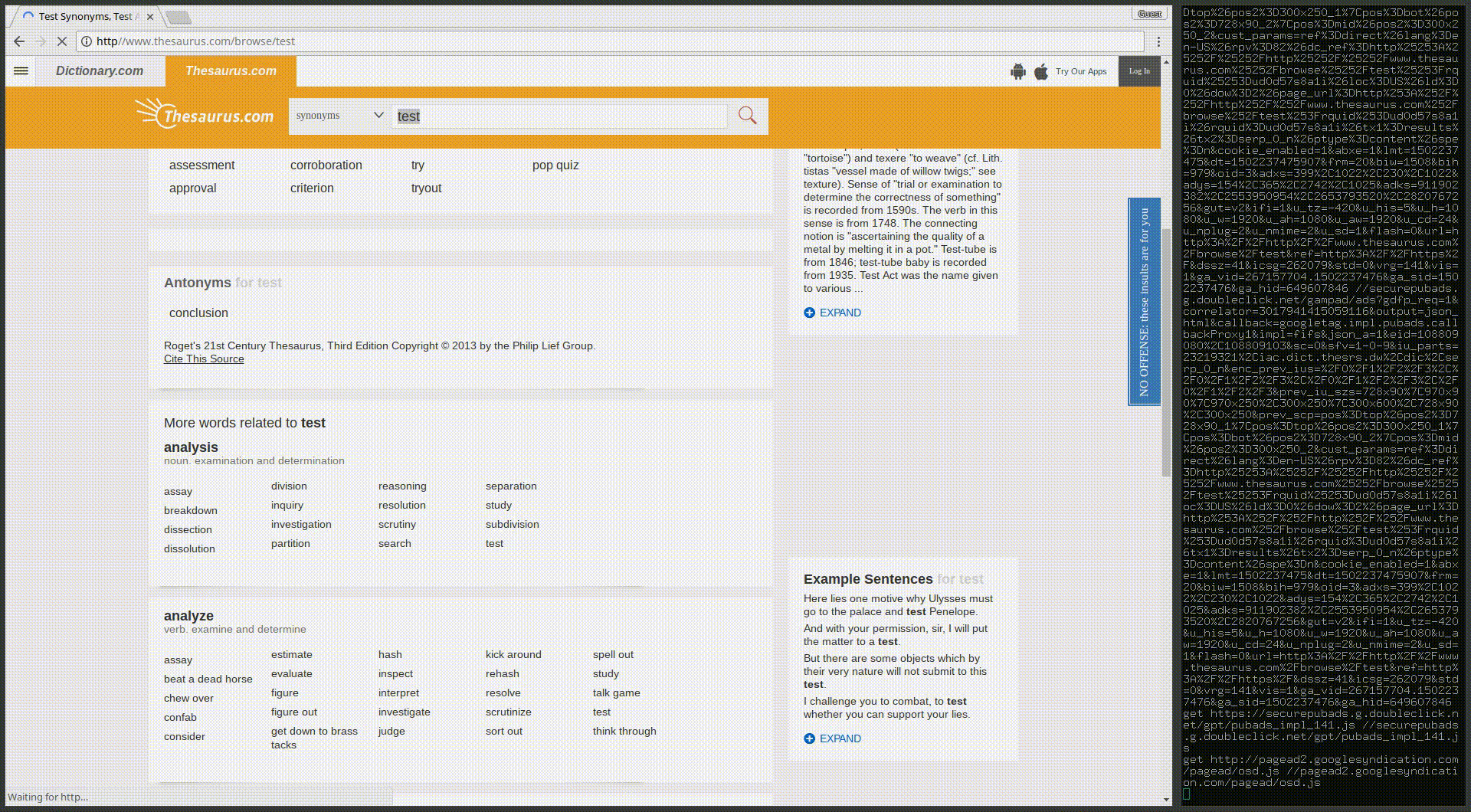

© 2025 Viam Technologies
